Last Update: 8/10/2024 (corrected missing graphic images)
This sounds simple, and is simple – but please remember that each piece is important. Each note has been placed with care.
$ sudo apt-get update
$ sudo apt-get install software-properties-common
$ sudo add-apt-repository ppa:certbot/certbot
$ sudo apt-get update
$ sudo apt-get install certbotThe following example is for the SPARELAB project we have been using as a unix shell. This provides a common context throughout this site.
This is going to request a Letsencrypt certificate for sparevpn.sparelab.net
In this case we are going to approach getting a certificate using the manual method.
We are going to use DNS as the method of verifying that we are in possession of the domain and may therefore – as the authorized users – may deploy the certificate they are so generously creating.
A quick note: We are using “-d” twice which essentially creates a SAN style cert with two different names in the address.
Side note: please note I made the RSA key size 2048.
certbot certonly --manual -d sparevpn.sparelab.net -d sparelab.net --agree-tos --manual-public-ip-logging-ok --preferred-challenges dns-01 --server https://acme-v02.api.letsencrypt.org/directory --register-unsafely-without-email --rsa-key-size 2048Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator manual, Installer None
Obtaining a new certificate
Performing the following challenges:
dns-01 challenge for vpnserver.sparelab.net
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name
_acme-challenge.sparevpn.sparelab.net with the following value:
hTLUOl7H1Y651ZpqugrFZcwF_CHz6ZFiqURIwwndk6c
Before continuing, verify the record is deployed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -A quick note: Before verifying this with Let’sencrypt remember to create BOTH TXT records for the request. Also if using BIND remember the “.” at the end of the text name. Remember to “Apply the configuration” or save or recycle and refresh the bind service.
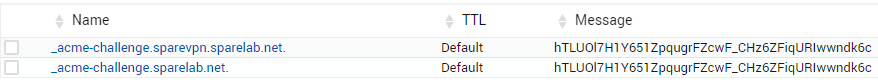
In this case we used MX-Toolbox – which makes for a impartial 3rd party witness – to verify the TXT record.
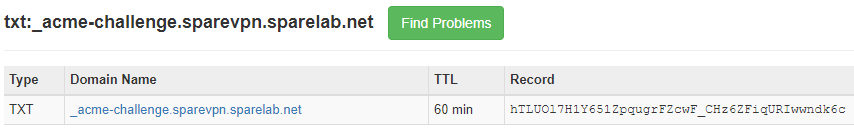
Not we can continue:
Press Enter to Continue
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/sparevpn.sparelab.net/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/sparevpn.sparelab.net/privkey.pem
Your cert will expire on 2021-03-20. To obtain a new or tweaked
version of this certificate in the future, simply run certbot
again. To non-interactively renew *all* of your certificates, run
"certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Just a quick note. I thought I would explore where all the results of our work occurred. It’s always good to know where the bodies are.
root@test:/etc/letsencrypt/live/sparevpn.sparelab.net# ls -al
root@test:/etc/letsencrypt/archive/sparevpn.sparelab.net# ls -la
total 24
drwxr-xr-x 2 root root 4096 Dec 20 20:42 .
drwx------ 3 root root 4096 Dec 20 20:42 ..
-rw-r--r-- 1 root root 2208 Dec 20 20:42 cert1.pem
-rw-r--r-- 1 root root 1586 Dec 20 20:42 chain1.pem
-rw-r--r-- 1 root root 3794 Dec 20 20:42 fullchain1.pem
-rw------- 1 root root 3272 Dec 20 20:42 privkey1.pem
The lion’s share of the work has been completed. We have one last step which is to create a PFX file for the ASA. This is important because then the ASA will need the private and public certificates as a chain and exported using a password.
root@test:/etc/letsencrypt/archive/sparevpn.sparelab.net# openssl pkcs12 -export -out /tmp/cert.pfx -inkey privkey1.pem -in cert1.pem -certfile chain1.pem -passout pass:l3tm3in
Now in /tmp/cert.pfx will be a binary chain that has a password associated with. The password is necessary because the ASA is going to request it. (<shrug> – when in Rome). I used Filezilla to transfer this file to my desktop. From here I used ASDM to upload it.
Note: To forestall an the obvious epic fail… please remember when using the VPN Anyconnect client to connect using your FQDN (ex: sparevpn.sparelab.net ) and not it’s IP address which will NOT match the FQDN on the certificate.
Note: if you keep the “test” box you used to create the cert, you will not have to go through the challenge of verifying yourself when you renew it. Remember the Letsencrypt certs are good for 90 days.
Reference:
https://medium.com/@timam/generate-let-encrypt-ssl-certificate-manually-febc949510c2
There should be a few other sites that detail this. There apparently also is a GIT for a plugin which uses the API and act’s as a go-between from the ASA to Letsencrypt. I have not tested the plugin.
END-POST

